
8 min read
- Seamless Edge and Multi-Cloud Operations — Unifying multiple cloud providers and private datacenters has been the holy grail for infrastructure and operations teams since the birth of cloud computing. Gartner estimates 9 in 10 enterprises will adopt Hybrid Infrastructure Management within two years. Enterprises want the flexibility to choose where to run their applications based on cost, speed to market, and security & compliance considerations. Distributing today's applications and a growing set of data services across multiple infrastructures (including private and edge computing environments) helps guarantee quality of service and uptime. Bursting workloads to the cloud, disaster recovery across locations, and simplified management of edge compute and remote offices is now effortless with DC/OS as your unified control plane. DC/OS 1.11 allows you to pool public cloud, private datacenter, and edge compute resources into a single logical computer and intelligently schedule workloads anywhere from a unified user interface.
- Production Kubernetes-as-a-Service — Development teams around the world are flocking to Kubernetes as their preferred platform for containerizing and deploying applications. But as an operator, your options for supporting these teams are less than ideal. Installing, operating, and upgrading Kubernetes on your own infrastructure can be challenging, and the loss of control and high cost of using cloud hosted container services can trump their convenience. DC/OS provides a third way: operations teams can deploy, scale, and upgrade pure Kubernetes for all of the teams in their organization with one click, and run their stateless applications alongside the stateful services that underpin them. Following a successful beta release of Kubernetes on DC/OS 1.10, during which the technology was tested by many users and customers, DC/OS 1.11 makes Kubernetes on DC/OS generally available.
- Enhanced Data Security — Every company's most valuable asset is its data. However, that data is also constantly under threat from bad actors around the world. To retain the trust of their customers, partners, and shareholders, every business needs to protect their data and applications. This latest DC/OS release adds multi-layer security features to help you secure your entire application stack.
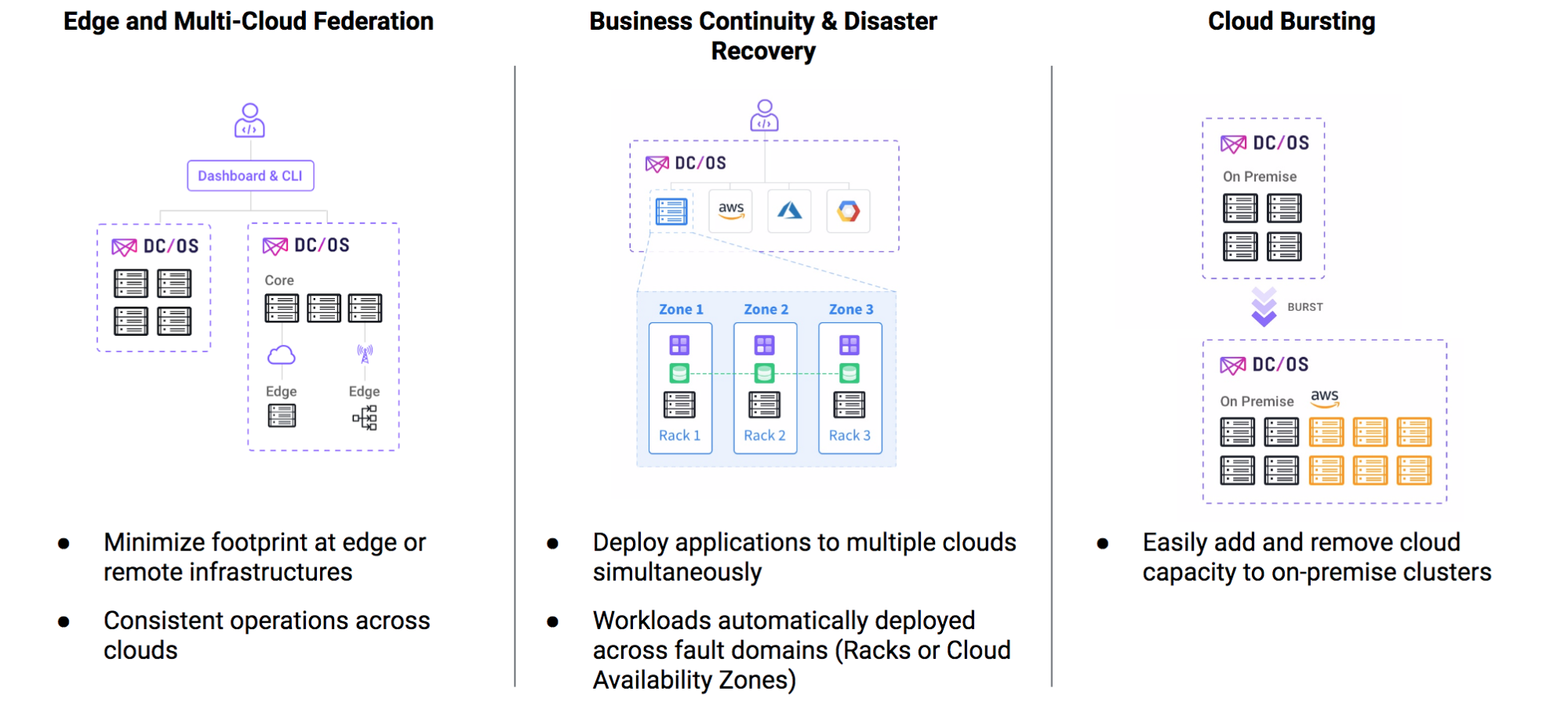
- An operator using his or her DC/OS credentials can manage multiple clusters on different clouds from a single DC/OS interface by linking these clusters. This means operators can focus on the services they're running, not the differences of the underlying infrastructure. Whether it's an on-premises datacenter, cloud compute on Azure, AWS, or Google, or any other mix of resources, the underlying infrastructure is transparent to the operator - simply use the dropdown menu to switch to the cluster you want to manage.
- DC/OS operators can also run clusters that are stretched, where the agent nodes (the servers that do the work) can be in a remote location away from the master nodes (the brains of DC/OS). This means operators can minimize complexity of their infrastructure by deploying only agent nodes in edge datacenter or remote offices (where they are needed), while still having a single unified operating experience across their entire infrastructure.
- Keeping applications highly available is another key challenge for infrastructure operations. Outages can occur at multiple levels including server, rack, datacenter (e.g., AWS US-EAST-1), region (e.g., AWS US-EAST) or the entire cloud (e.g., all of AWS).
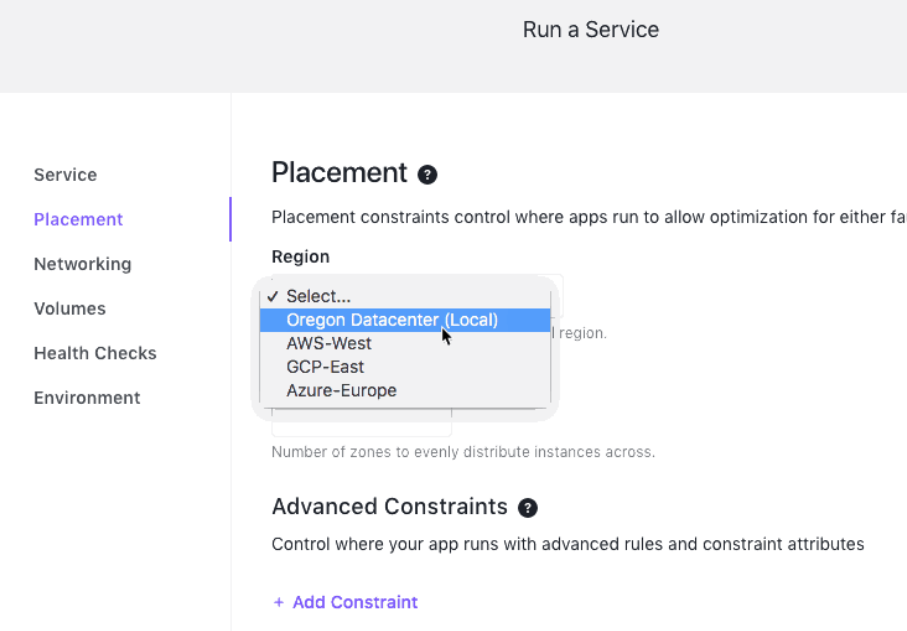
- DC/OS 1.11 allows operators to intelligently define fault domains and recover against this hierarchy to maximize service survivability. For example, within a region, stateless services can recover automatically from failures at the node, cluster, rack, or even site level. For stateful services, Mesosphere has partnered with Portworx to provide persistent storage for containers that is fully integrated with DC/OS, so users can easily run stateful services with highly available storage, bare-metal performance, and built-in data protection.
- DC/OS allows operators to easily deploy workloads to multiple regions (e.g., to AWS, and also on Azure), to enable multi-cloud high availability.
- DC/OS makes it effortless to set up highly available Kubernetes for production — it automates 20+ steps and many hours (or days) of work into a single click, resulting in a fully functional deployment in minutes.
- Scale Kubernetes up or down for a seamless cloud-like experience.
- DC/OS automates Kubernetes installation on any infrastructure — AWS, Google Cloud, and Azure (using Terraform templates).
- We use the pure, open source version of Kubernetes - and always will.
- Count on the latest version of Kubernetes as soon as you're ready for it. Upgrade your Kubernetes deployment to the latest version in-place, without disruption, due to DC/OS application-aware automation.
- Teams typically run Kubernetes with other tools to facilitate operations and support a delivery pipeline. Examples include Prometheus for monitoring, Jenkins for continuous integration/continuous delivery (CI/CD), and Elastic, Logstash, & Kibana for logging. All of these services run elastically together on a shared DC/OS cluster.
- The same DC/OS Kubernetes cluster also runs backing data services and machine learning tools such as Apache Spark, Apache Kafka, Apache Cassandra, & TensorFlow.
- Transport layer security (TLS) ensures only trusted services can communicate with each other (server-to-server), and their client communications are also encrypted (server-to-client). For example, TLS ensures that two nodes of a Cassandra or Kafka cluster can communicate securely, by encrypting the network traffic between those nodes.
- Internal certificate authority automatically generates and dynamically distributes the required encryption certificates and configures the associated application.
- Encryption keys and certificates are securely stored in DC/OS's encrypted secret store and dynamically loaded only for authorized services or clients, providing an additional level of security for your sensitive data.
- By enabling client authentication for connections to application or data services, you can control which applications can read or write to those data services. Authentication mechanisms can include Kerberos, LDAP, or Active Directory protocols.
- Fine-grained client authorization and control over read and write operations. For example, you may decide to have only certain applications read or write to a specific topic within the Kafka service on DC/OS.
- DC/OS provides a centralized encrypted and access-controlled location for sensitive application credentials such as username/password, certificates and configuration files. Applications are automatically loaded with the right credentials at launch.
- DC/OS 1.11 adds a hierarchy, and multi-team isolation to the DC/OS secrets store, making it easier to manage which secrets can be accessed by various applications or teams.








